How many vulnerabilities will your devices face until end of life?
How much longer will your devices be in the field?
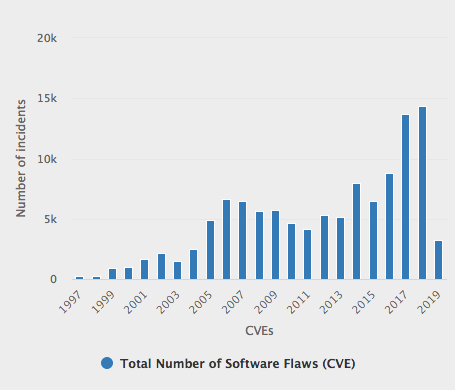
Reported Linux vulnerabilities since launch in 1997*

Software Flaws (CVE) Trends
Linux devices are not invulnerable. Indeed, one of Linux's greatest strengths is the rapidity of the community’s response to security vulnerabilities.
Reported Linux vulnerabilities since launch in 1997*

Software Flaws (CVE) Trends

With Wind River, you can rest easy knowing that the Wind River security team is constantly monitoring the Common Vulnerabilities and Exposures (CVE) database at cve.mitre.org for potential issues affecting Wind River Linux and Wind River Pulsar™ Linux.
Our security team is monitoring specific security notifications from US Government agencies and organizations like NIST, US CERT, and also public and private security mailing lists, and receives email alerts from each of these organizations whenever a new security threat arises. Alerts include both community-confirmed and potential vulnerabilities—we look into all of them. Participation in these forums gives Wind River the opportunity to create patches for vulnerabilities even before the community publicly announces the vulnerability.
We keep you safe in four ways:
All the kernel features, user packages, and Linux tools, which are supported in the standard Wind River Linux distributions, are monitored for security vulnerabilities against the incoming reports.
When Wind River is notified of a potential vulnerability by one of the monitored advisory groups, we first determine whether any supported Wind River product is actually susceptible to the vulnerability.
Once the assessment phase is complete, we notify customers of the level of susceptibility.
Less severe vulnerability patches are delivered via the monthly product updates.










“Wind River Linux provides the security, scalability, and flexibility we need.”
—Nicolas Letterier, CTO, Schneider Electric